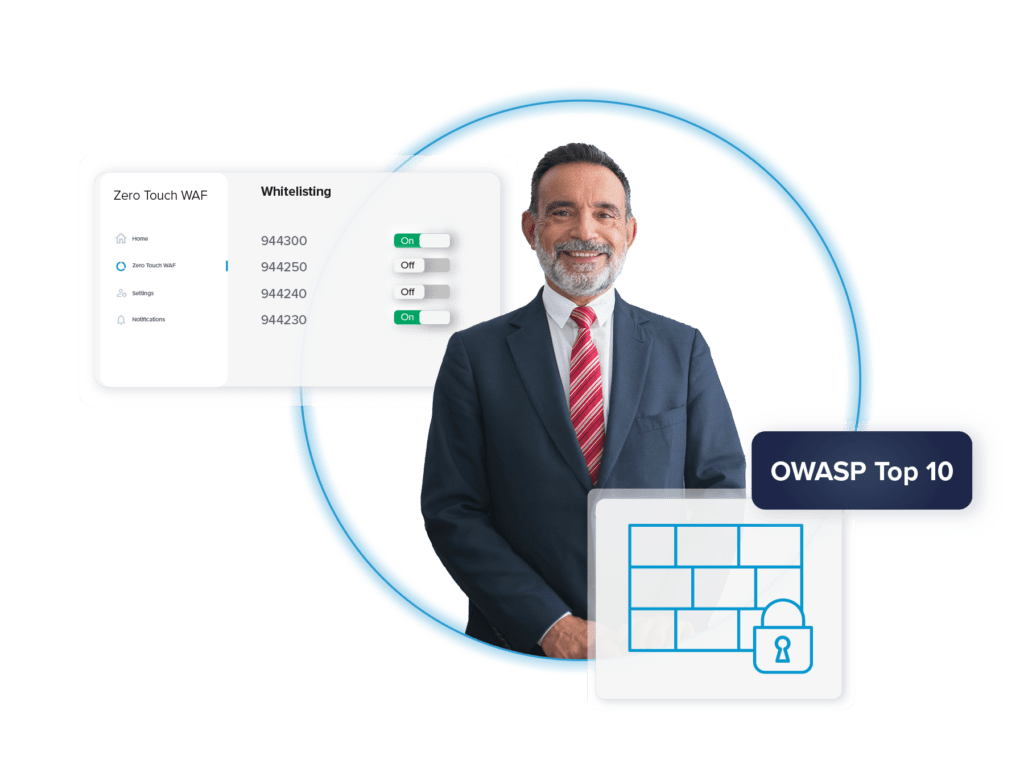
Zero Touch WAF
- Effective protection against zero-day vulnerabilities
- Whitelisting rules to customize personal preferences
- Automated protection available right out of the box
Our WAF product ensures effortless protection by proactively identifying and defending against a myriad of threats at all times.
Empower your strategy with bespoke WAF rules that allow you to design custom rules that fit your website or application needs.
Customize your protection by flexible whitelisting rules to align with your customized/special website or application design.
Unpatched software is still considered a dangerous gateway for cybercriminals today. The use of global exploits is not decreasing; the numbers keep increasing. To avoid relying on software support, you should rely on our Zero Touch WAF, which detects and stops such unwanted events.
In case of a threat, you should rely on a regularly updated WAF that effectively protects you from current threats. That’s why our Zero-Touch WAF is regularly updated and actively updated with new protection rules. This flexibility means you get increased and constantly updated security against zero-day threats, which is a step ahead of many larger WAF vendors due to its agility.
Virtual zero-day patching and coverage of the OWASP Top 10 rules guarantees you a high level of protection that always stays up to date. Important for you: we take care of all that. You always enjoy a high level of protection and don’t have to worry about anything else.

If you wish, you can design your WAF rules to tailor the protection solution as precisely as possible to your needs. Add this to the stored rules, incorporating our experience and an overview of the current security situation. This flexibility, combined with years of industry experience, opens up completely new possibilities for you.
The whitelisting rules also play an important role here: they allow you to customize the protection yourself, which is ideally suited to the design of your website or application. Ensure that your unique elements are preserved without compromising security.

One reason is that cybercriminals can use DDoS attacks as a diversionary tactic to access personal data. Link11 Zero Touch WAF reliably detects web application attacks such as SQL injection, XSS, and CSRF if they’re part of OWASP Top 10 and blocks the malicious requests to ensure 24/7 availability of web resources. When WAF is deployed as an add-on to our DDoS Protection, its performance is maximized, and you benefit from additional security.
Our security solutions are constantly evolving and always adapting to market conditions. New threats are thus quickly identified and included in the rule set.
For more than 10 years we have been taking care of the cybersecurity of global customers and have gained valuable experience.
Our security solutions are all automated and require no action from you to reliably protect you around the clock.
With the help of our experts, the security solutions are implemented into the existing setup for you in an uncomplicated and time-saving manner.
Our experts are available around the clock to provide you with advice and assistance. We take as much time for you as you need, in German or English.

“The Link11 specialists have always provided us with professional and expert support. The work was done in a responsive and cooperative manner and you could always count on a response the following business day at the latest.”
Manager Cloud Computing
Genesys Informatica
Together, we will create a customized solution for your Zero Touch WAF. Our security experts will be happy to support you and advise you without obligation on the benefits of our Link11 solutions for your company.